Version 2.6 brings Favorites, Custom Filters and more
Secrets 2.6, for both macOS and iOS, is now available. This release delivers on some of the most commonly requested features.
Favorites
When you open Secrets you’ll find a new built-in filter called Favorites. Simply tap the ★ button on the item detail to add it to your favorites. Tap again to remove it.
You can mark any item as a favorite, be it a Login, Credit Card, Note, etc. Quickly access them by selecting the Favorites filter.
One interesting thing to note is that this feature is actually built upon the tagging feature we introduced in version 2.4, and it serves as an example of what you can do with Custom Filters.
Custom Filters
Previously, Secrets added the ability to tag your items. By tagging your items Secrets could surface more relevant results when searching.
With this update, you don’t even need to search. If you have a group of related items you access frequently, you can create custom filter and have those items at a click distance.
You can use much more than tags to create your custom filters. Want to see all Logins you’ve created using a specific e-mail as username? Sure. Want to see which Logins have a One-Time Password set? You can do that too!
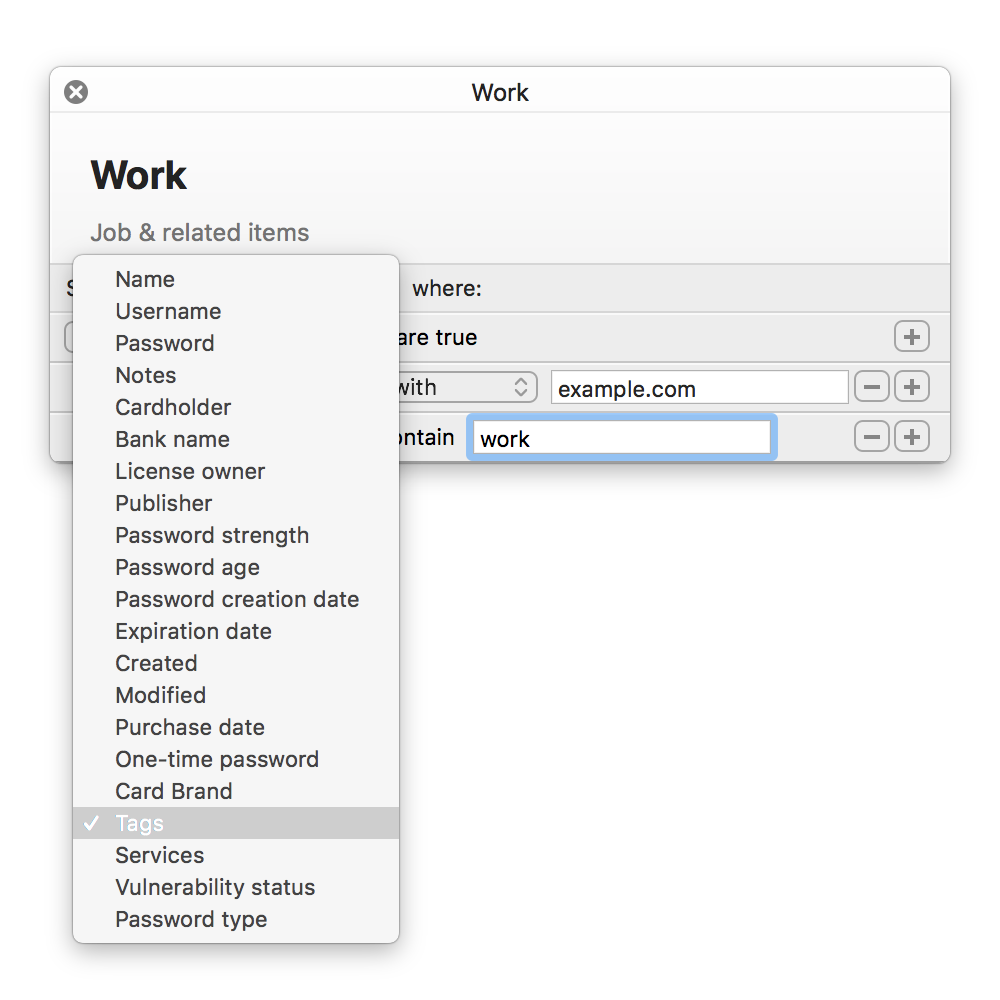
Custom filter options
Some of our users have asked for folders. This is our answer to that. Custom filters are much more flexible than folders and can easily achieve the same effect. Simply tag your items with what the folder name would be and create a filter based on that. With the advantage that the same item can belong to more than one “folder”.
Vulnerability check
Last but not least, you can check your Logins against the popular Have I Been Pwned service.
This service collects data, such as usernames and passwords, exposed on the internet from various service breaches. It then makes this data publicly available and easily queryable.
Secrets will check both if your username is contained in any of the breaches collected, and if your password was leaked. Worth noting, is that your password is never sent to the service, only the first 5 characters of the SHA1 hash of your password is sent. If you want to know more about how this works, the author Troy Hunt, does a great job explaining it in this blog post.
One final remark, is that Secrets will never consult this service without you explicitly telling it to do so. We don’t want Secrets to do anything behind your back, even if it could potentially find vulnerable logins for you.
